Typically the GPL covers the source code. Compiled, packaged and branded binaries are sometimes licensed separately. This is how Red Hat works for example.
- 19 Posts
- 145 Comments
I get it. We should be skeptical of what we hear from influencers on social media. IMHO the way to debunk pseudoscience is with real science. There is some amazing scientific work done in this area and I wanted to highlight that.


My Nespresso maker was stolen.
I have a fancy Delonghi Nespresso machine in the coffee nook space at my office. One morning I go to make my usual oat milk latte to find my machine is gone! I contacted building security who informed me there is no camera on our floor.
After scouring several floors in my building, I was ready to give up. Talking to some of my co-workers they suggested sending a mass email out to the teams that had recently relocated from our office. I proceed to do so. Turns out our new CEO is in our building and was in on of the building email lists. So my first interaction with the new CEO is to accuse them of stealing my coffee machine!
It turns out that this was more a Three’s Company episode than a CSI episode. One of the other teams had made a request for their own machine and when they moved, had assumed it belonged to them and slapped a moving sticker on it. In the end I hot my machine back. Hopefully I don’t get sacked by the nee CEO!
I know the idea is to be snarky and calling them “new age” somehow makes them less than real science, but the reality is there is some amazing science that has been done that shows how these different chemicals influence our brains and our behaviors. Good video on the topic with in-depth explanations from real scientists:
HAPPINESS: A Guide to the Drugs That Can Help You Get There -> https://www.youtube.com/watch?v=zcAmgNoWzVk&t=29s
The scientist in the video:

From the article:
Practical advice for building and improving tolerance as well as preventing symptoms and exacerbations
Primary prevention Support breastfeeding, with solid foods from 4–6 months onwards Do not avoid exposure to environmental allergens (foods, pets), if not proven necessary Strengthen immunity by increasing contact with natural environments (e.g. by taking regular physical exercise and following a healthy diet such as a traditional Mediterranean or Baltic diet) Antibiotics should only be used in cases of true need (the majority of microbes are useful and build a healthy immune function) Probiotic bacteria in fermented food or other preparations may balance the immune function Do not smoke (parental smoking increases the risk of asthma in children) Secondary and tertiary prevention Regular physical exercise is anti-inflammatory Healthy diets are anti-inflammatory (a traditional Mediterranean or Baltic diet may improve asthma control) Probiotic bacteria in fermented food or other preparations may be anti-inflammatory Respiratory/skin inflammation should be treated early and effectively; maintenance treatment titrated for long-term control To stop symptom exacerbations proactively, instructions for guided self-management are provided for 10 allergic conditions (available in both paper and electronic formats) Allergen-specific immunotherapy is recommended for more severe symptoms, e.g: allergens as such (for foods) sublingual tablets or drops (sublingual immunotherapy, or SLIT) (for pollens) subcutaneous injections (for pollens, pets, mites, insect stings) Smoking should be strictly avoided (the effectiveness of asthma and allergy drugs is reduced in smokers)


Go read the FIDO threat model if you want to understand how it protects against specific attacks. It is pretty secure.
https://fidoalliance.org/specs/fido-v2.0-id-20180227/fido-security-ref-v2.0-id-20180227.html


Jet Lag


It is hard to do well which is why I worry. Google probably has the best overall account security, you could fo worse than modeling after them.
The short answer to your question is Passkeys. But you need a whole system of account recovery around them.


I love Lemmy and Voyager and the Fediverse. That said, if it were to become mainstream I forsee some problems. The fact that the login relies on only passwords is pretty terrible. Also, this makes the service vulnerable to bots, sock puppet accounts, brigading, etc.
We have come so far through the application of rationality and the scientific method. All the wonders of the modern world we owe to science.
What has pseudoscience bought us? Ignorance and stagnation.
I want to live in a world of technological progress not a “Demon Haunted World.”


Anytime I post about AI or LLMs I get aggressively downvoted.
I do not do it very often and when I do it usually a gee whiz, look at that post. Inevitably the response is AI slop!!! AI is bad, you are bad , you should feel bad.
What are you scared of?
If you are worried your parents will see your browsing history, that is you threat model.
If your concern is government surveillance, you need to do more than just clear your browsing history.
So basically its its own genre.


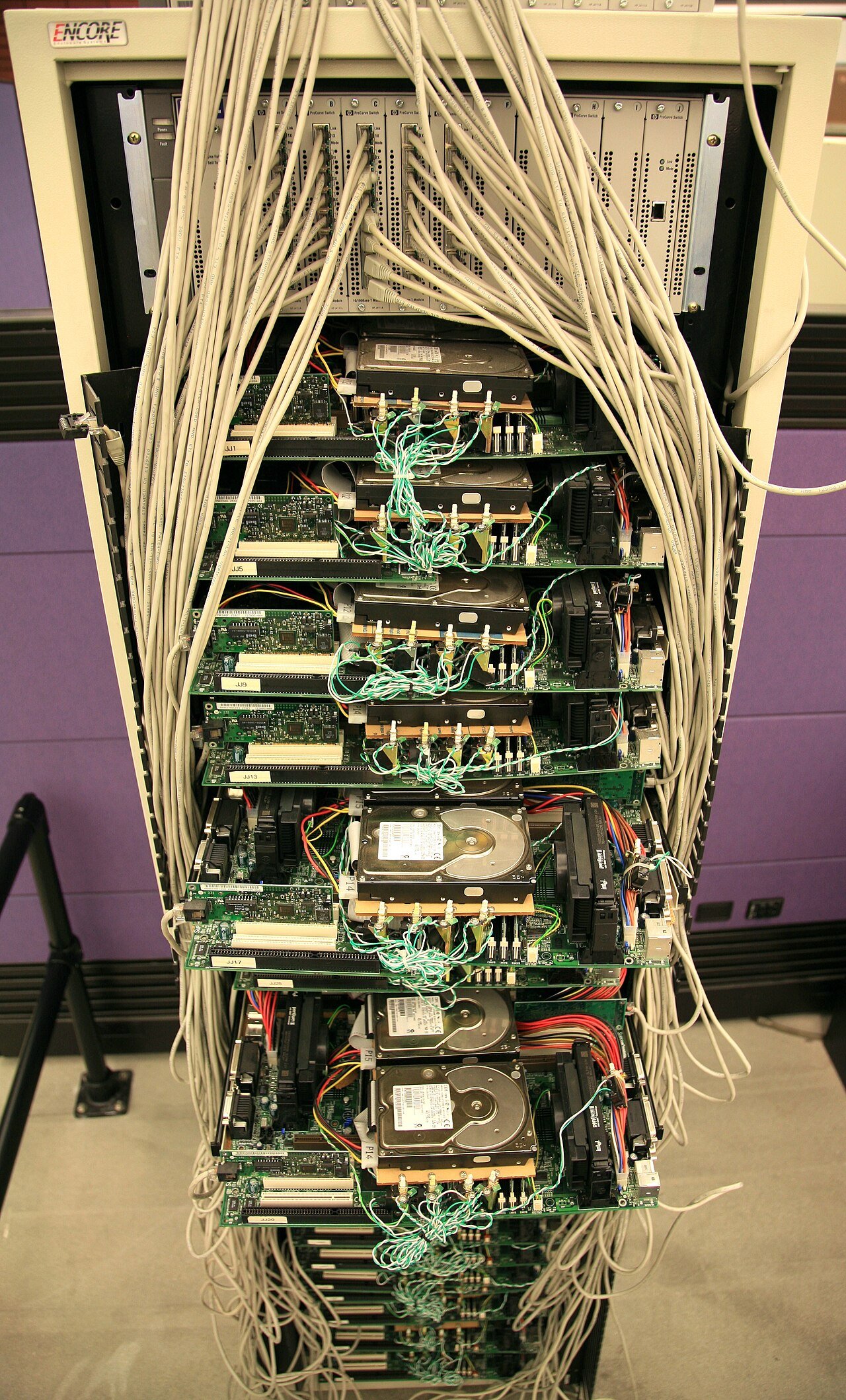
A PC can be a server. A server can be a PC.
Famously Google use commodity PC hardware to build the v1 version of its search engine:
Day of Defeat source players:
https://steamcharts.com/app/300#All
Its like being on an island that is slowly sinking into the sea.


Source mod tools not to be confused with Sourcemod tools.


I can only speak for myself and my kids. I have an iPhone because my work gave me one for free. They only support iPhone for security reasons. Keeping Android devices up to date across a large fleet is challenging leaving security gaps. For my kids they wanted my old iPhones because it’s what all their friends have.


I feel like OP missed an opportunity to title this post “Fedora Flatpaks Fall Flat”
Great article, BTW


The answer to your question is zero yet at this he same time zero is not an answer to your question.

















He likely hasWatch out for rabies.